Blocking the Nvidia certificates on your machine
This quick guide shows how to block the leaked certificates using the command line or graphical utilities.
There are multiple certificates (download links at the very bottom). You need to perform the installation steps for all of them
You can click on the thumbnails to enlarge them for a visual aid
Installation using the command line
You can install the certificate using a single command in an elevated command prompt.
Download The leaked certificates (links at the bottom), then run this command in an elevated command prompt for each certificate:
certutil -addstore Disallowed C:\Path\To\Cert.crtYou either need to supply the full path to the certificate or use the CD command to enter your download directory
Installation using graphical utilities
If you're not used to the terminal, you can perform the steps using built in Windows utilities.
1. Download and install
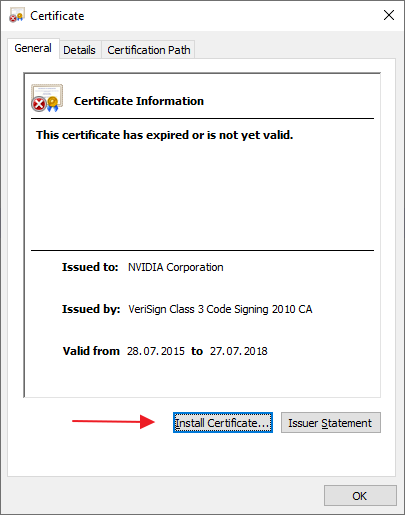
Download the leaked certificates (links at the bottom). Open the certificate and click "Install Certificate..." button
2. Select store type
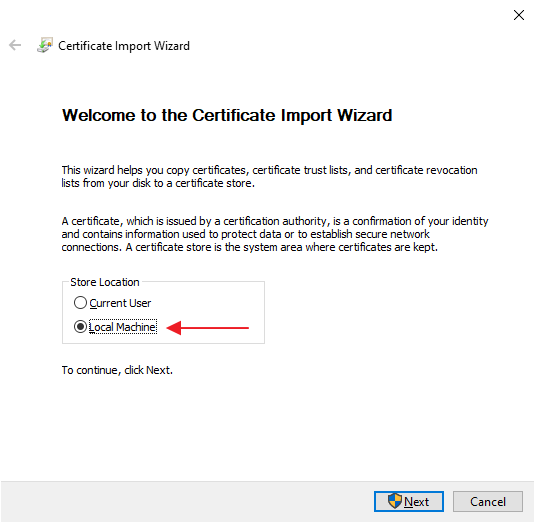
Select "Local Machine" and click "Next"
3. Select location
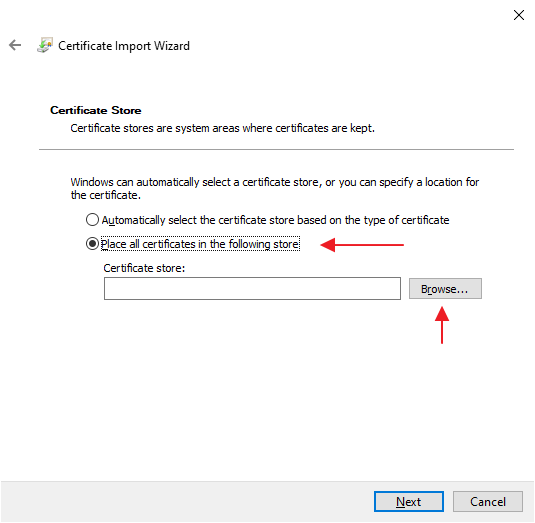
Select "Place all certificates in the following store" and click "Browse"
4. Select distrusted store
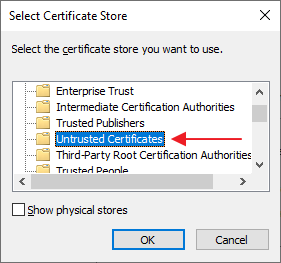
Select the "Untrusted certificates" store and click "OK", then click "Next"
5. Confirm
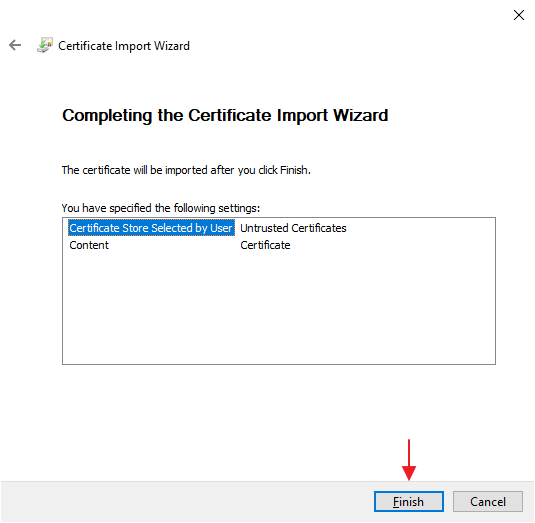
Click "Finish" to complete the installation
6. Verification
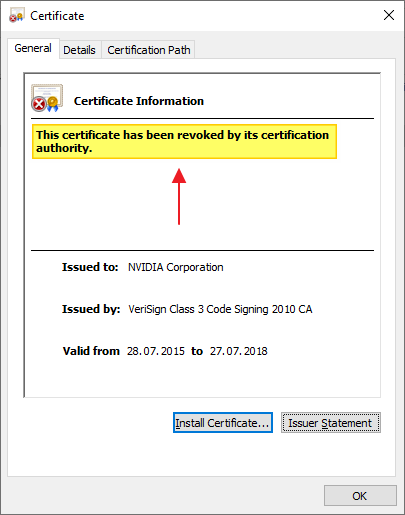
To verify that the certificate has been installed, close the certificate window if it's still open, then reopen the certificate.
The text should now say that the certificate has been revoked.
Installation check
You can check if the cert is installed as revoked by running the command below in a command prompt:
certutil -store Disallowed 30632ea310114105969d0bda28fdce267104754f
certutil -store Disallowed c0d71b4c5a1aa1f6e2c5d9ba4556c85663f7ed27
certutil -store Disallowed 579aec4489a2ca8a2a09df5dc0323634bd8b16b7If installed, the certificate is shown.
"CertUtil: Object was not found" is shown if it's not installed.
Uninstallation
STOP! THE CHAPTERS BELOW EXPLAIN HOW TO UNDO THE STEPS ABOVE. DO NOT PROCEED UNLESS YOU WANT TO ENABLE THE CERTIFICATE AGAIN
Using command line
Run this in an elevated command prompt to remove the certificate
certutil -delstore Disallowed 30632ea310114105969d0bda28fdce267104754f
certutil -delstore Disallowed c0d71b4c5a1aa1f6e2c5d9ba4556c85663f7ed27
certutil -delstore Disallowed 579aec4489a2ca8a2a09df5dc0323634bd8b16b7With a user interface
To uninstall the certificates, follow these steps:
- Download and run Certificate manager++
- Open the "Local Computer" certificates
- Open the submenu "Untrusted Certificates", then the submenu "Certificates"
- Delete the "NVIDIA Corporation" certificates by selecting them and pressing the
DELETEkey, or using the context menu, or the red ❌ in the toolbar.
Download links
These are the certificates you want to block
- Cert 1
- Cert 2 (we do not have a private key to this one, but blocking it should not cause any problems due to the age of the certificate)
- Cert 3
Private keys
We do possess private keys for certificates 1 and 3 and can confirm that these keys are contained in the leaked data and trivially obtainable due to hardcoded passwords.
You can get random test data signed using the key here
Maybe consider this a lesson about proper storage of private keys.
Safe handling of keys
A safe way of handling private keys is to not have them internet accessible by means of being physically disconnected.
- Store the keys on a machine that has no internet access
- On another computer, generate the hash of the executable that needs signing
- Transfer the hash over to the computer with the key
- Use a hardware device locally on the key computer to unlock the key and sign the hash
- Transfer the result back to the computer that has the executable
- Embed the signature in the executable and timestamp it
How to perform step 3 and 5
Using passive media (media that doesn't requires active negotiation like USB does). This includes floppy disks. You still only want to transfer the hash and signature instead of the executable to avoid and potential vulnerabilities for when the OS tries to read executable properties.
Another possibility is via a serial cable link.
If you feel more modern, you can connect a webcam and printer to the computer so it can scan and print QR codes. Transferring data via audio is also possible. Audio tape based storage was actually a cheap and popular way to store data in the 70s and 80s for home users, and all modern computers have audio inputs and outputs.
Does this actually work?
Currently not.
The tool used to sign windows based software (signtool.exe from Microsoft)
does not support generation of hashes and import of remotely made signature data.